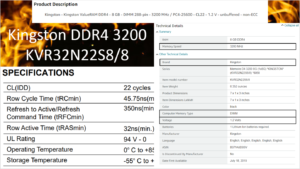
It’s Freakin’ Insane!
Yo, gamers! Tired of your PC lagging out like your grandpa’s dial-up internet? Want frames so smooth you could butter them on toast? Then ditch your dusty DDR4 RAM and get ready to unleash the beast with Kingston FURY Beast DDR5 memory!

This ain’t your average RAM upgrade, it’s a full-on performance overhaul that’ll leave your old setup whimpering in the corner. We’re talking speeds that’ll make your games feel like they’re on fast forward, load times that vanish quicker than your lunch money.
But hold on, there’s more! This beast ain’t all bark and no bite. Kingston FURY Beast DDR5 rocks something called “ODECC” tech, which basically means it protects your data like a mama bear guards her cubs. No more crashes or stutters, even when you’re pushing your PC to the limit. Plus, it’s got this sweet heatsink that keeps things cool under pressure, so your RAM won’t throttle down like a car with a busted radiator.
And let’s not forget the looks! This RAM ain’t just fast, it’s stylish too. With a sleek design and optional RGB lighting, you can personalize your rig to match your gamer vibes. Whether you’re feeling like a neon ninja or a blackout assassin, there’s a Kingston FURY Beast DDR5 setup that screams “you.”
So, here’s the deal: if you’re serious about gaming and want the best performance your money can buy, then Kingston FURY Beast DDR5 memory is the upgrade you need. It’s like having a cheat code for your PC, giving you the edge you need to dominate the competition and level up your game like a boss. Trust me, once you experience the beastly power of DDR5, you’ll never go back. Just don’t say I didn’t warn you – your friends might accuse you of hacking when they see how smooth your gameplay is!
Note: This review is part of a classroom project.
Resources:
https://www.kingston.com/en/memory/gaming/kingston-fury-beast-ddr5-memory
https://gemini.google.com/