The Intel Core i5-9600KF is a relatively inexpensive Intel CPU (Central Processing Unit.) The CPU is the brains of a PC. Intel is the oldest, most established maker of CPUs. This CPU would be great for a gamer PC. It is a 9th generation processor (the newest models from Intel at the time of posting) and runs at a frequency of 3.7 GHz.
Frequency is the speed at which a CPU handles information. In this case, the CPU works at 3.7 billion cycles per second. FYI, that is alot. This CPU ranks at 254 on the PassMark rating, but it’s price and performance make it more than good enough for a gamer PC.
Two other really important things to consider when buying a CPU are computing cores and memory. The i5-9600KF has 6 cores, meaning it can compute 6 different processes at the same time. More cores means that more things can be happening in the background without slowing down the overall performance of the system. The memory on this CPU is 9MB of L3 cache. This is memory that the cores use while it is handling the processing on the system. 9MB is about mid-range, but will again be sufficient for a gamer PC.
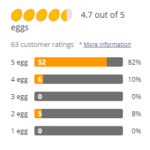
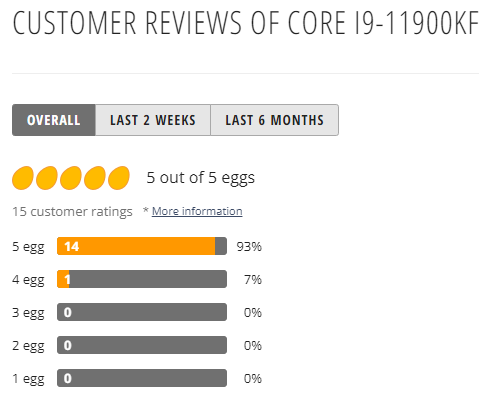
The reviews on this CPU are actually great on NewEgg. NewEgg gives it 5 eggs(the best possible) and you can read all the reviews by clicking the image below.
I should also note that this CPU will automatically increase its speed to 4.6GHz when needed, this is called the “Turbo” frequency.
This CPU needs to be paired with a motherboard with an LGA1151(300 series) socket. Any other motherboard type will not work. It will support DDR4 2666 memory on the motherboard, which will also be a consideration when making related purchases. Finally, a good CPU cooling solution needs to be purchased for it, this CPU does not come with a stock fan.
I highly recommend this CPU for purchase! It will make a very responsive gaming system, as well as supporting any other needs (like research and homework.) It is currently listed for $217.89 at NewEgg and $206.99 at Amazon. Since the price is less, and shipping is free, I would recommend the purchase at this time from Amazon.
Works Cited
“Intel Core i5-9600KF @ 3.70GHz.” PassMark, www.cpubenchmark.net/cpu.php?cpu=Intel%2BCore%2Bi5-9600KF%2B%40%2B3.70GHz&id=3443.
“NewEgg.com.” NewEgg.com, www.newegg.com/core-i5-9th-gen-intel-core-i5-9600kf/p/N82E16819117996.
Note: This review is part of a classroom project